Ensuring strong security measures for cloud platforms such as Microsoft Azure is critical in today's digitally connected society. Azure offers a full range of services and … [Read more...] about Maximizing Security on Azure: Best Practices and Tools
Blog
Getting Started with Microsoft Azure: A Beginner’s Guide
Cloud computing has completely changed how organizations function in today's digital environment by providing scalable, adaptable, and affordable solutions. Microsoft Azure, a … [Read more...] about Getting Started with Microsoft Azure: A Beginner’s Guide
Emerging Technologies: Google Trends Insights
Keeping up with developing technologies is essential for innovators, consumers, and organizations in today's quickly changing technology scene. Google Trends is a useful tool for … [Read more...] about Emerging Technologies: Google Trends Insights
Strategies for Scaling Applications on AWS
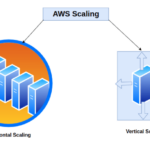
The capacity to scale programs effectively and resiliently is essential in the rapidly changing cloud computing environment to preserve performance, control expenses, and guarantee … [Read more...] about Strategies for Scaling Applications on AWS
Serverless Applications with AWS Lambda and API Gateway
Serverless architecture has completely changed the way applications are created, implemented, and scaled in the context of cloud computing. Important capabilities provided by … [Read more...] about Serverless Applications with AWS Lambda and API Gateway